Why Use an eID Broker?

Why Use an eID Broker?
4 December 2024
1
min read
How Cryptography Is Used in Digital Identity


How Cryptography Is Used in Digital Identity
3 December 2024
4
min read
How Does Identity Theft Work?


How Does Identity Theft Work?
1 December 2024
6
min read
Zero-Knowledge Proofs: A Beginner's Guide
Zero-Knowledge Proofs: A Beginner's Guide
12 September 2024
10
min read
How to Authenticate Callers with Twilio, CIBA, and the Swedish BankID Phone Authentication


How to Authenticate Callers with Twilio, CIBA, and the Swedish BankID Phone Authentication
4 July 2024
10
min read
An Introduction to Client Initiated Backchannel Authentication (CIBA)
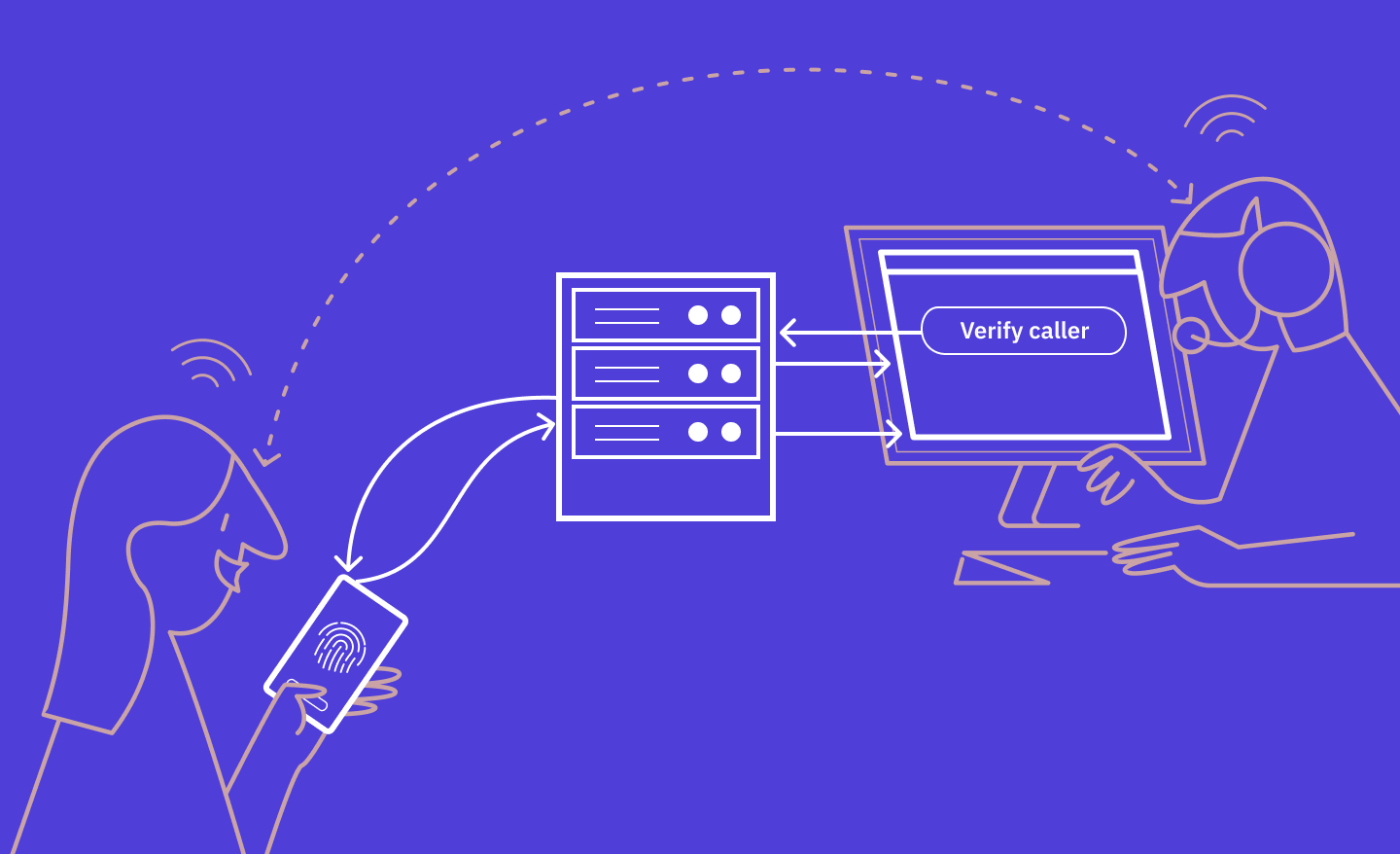

An Introduction to Client Initiated Backchannel Authentication (CIBA)
31 May 2024
4
min read
What Are SD-JWT-based Verifiable Credentials?


What Are SD-JWT-based Verifiable Credentials?
21 March 2024
7
min read
Verifiable Credentials: A Glossary (For Everyone)
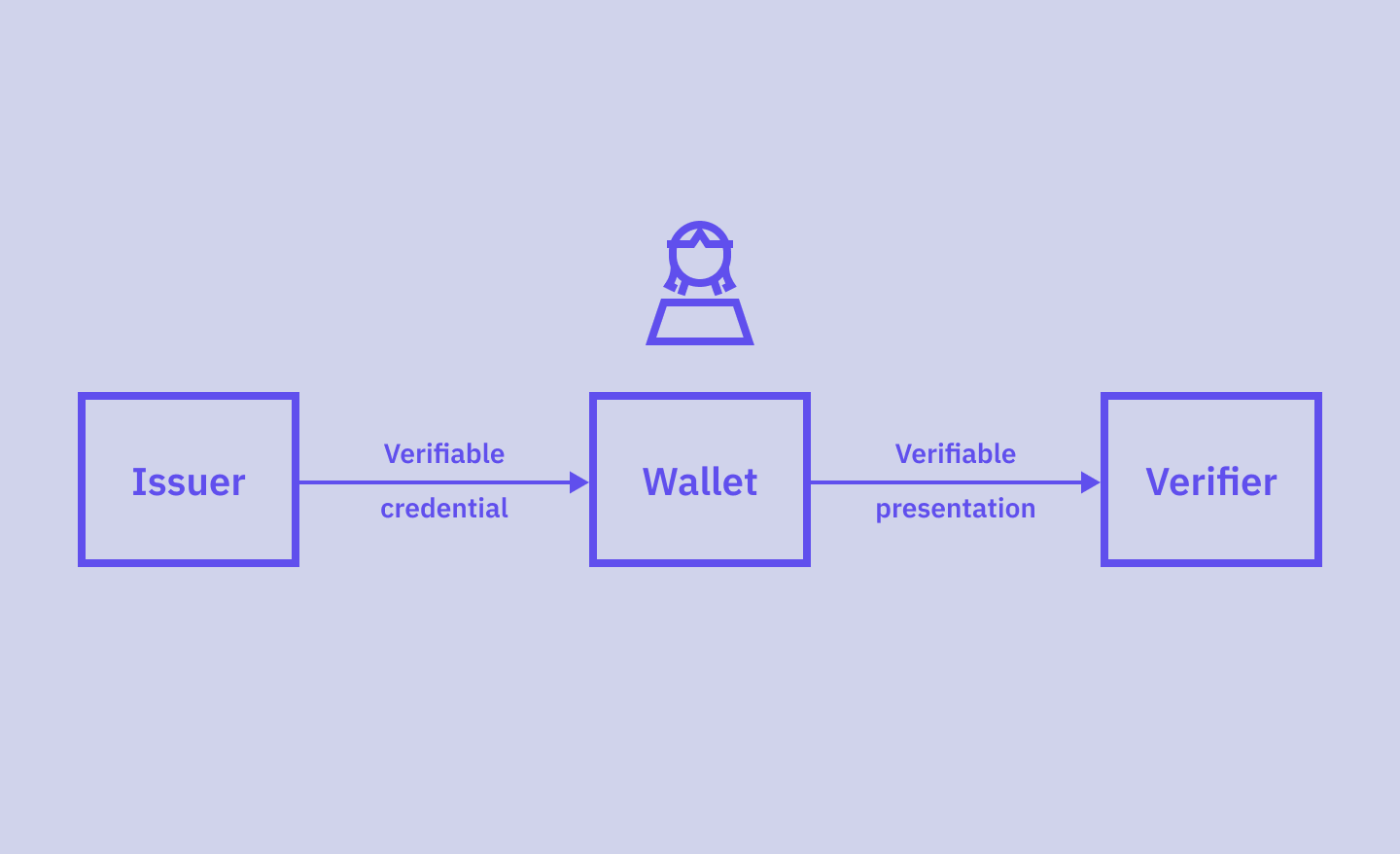

Verifiable Credentials: A Glossary (For Everyone)
1 March 2024
7
min read
Understanding JWT Validation: A Practical Guide with Code Examples


Understanding JWT Validation: A Practical Guide with Code Examples
22 January 2024
11
min read
How To Use Fiddler to Debug Authentication Flows


How To Use Fiddler to Debug Authentication Flows
12 December 2023
9
min read
Cryptography 101: What Is Hashing?


Cryptography 101: What Is Hashing?
13 November 2023
6
min read
Trusted Timestamping: Comprehensive Guide & Use Cases


Trusted Timestamping: Comprehensive Guide & Use Cases
6 November 2023
5
min read
