Verifiable Information: An EU initiative to increase trust and reduce cost
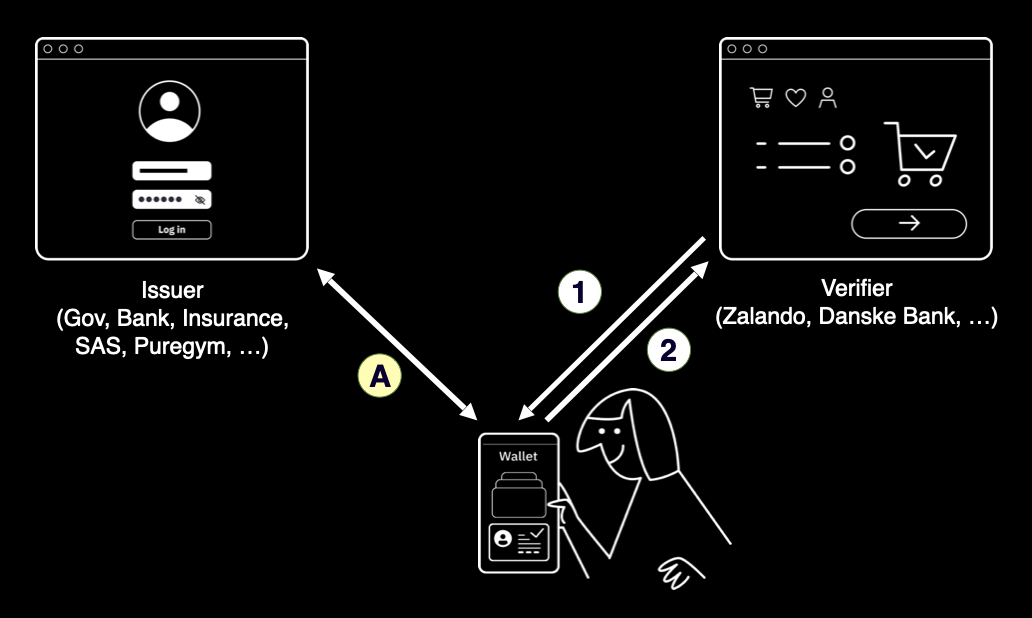

Verifiable Information: An EU initiative to increase trust and reduce cost
20 November 2025
8
min read
Why Caller Authentication is a Better Way to Verify Identity on the Phone


Why Caller Authentication is a Better Way to Verify Identity on the Phone
20 October 2025
2
min read
Digital Identity in Europe Depends on More Than Wallets


Digital Identity in Europe Depends on More Than Wallets
7 October 2025
2
min read
Practical Guide to FTN Compliance & the Idura Compliance Checker

Practical Guide to FTN Compliance & the Idura Compliance Checker
21 August 2025
3
min read
5 Reasons Verifiable Credentials Are Not Yet Widely Adopted


5 Reasons Verifiable Credentials Are Not Yet Widely Adopted
9 July 2025
3
min read
10 Use Cases for Verifiable Credentials


10 Use Cases for Verifiable Credentials
9 July 2025
4
min read
6 Business Benefits of Verifiable Credentials


6 Business Benefits of Verifiable Credentials
9 July 2025
5
min read
Why Signed Authorization Requests Elevate Your Security


Why Signed Authorization Requests Elevate Your Security
25 June 2025
4
min read
Private Key JWT: A Stronger Alternative for Client Authentication


Private Key JWT: A Stronger Alternative for Client Authentication
18 June 2025
3
min read
Securing Authentication Flows with JSON Web Encryption


Securing Authentication Flows with JSON Web Encryption
18 June 2025
3
min read
JSON Web Encryption: How It Works, Why Important, and When to Use It


JSON Web Encryption: How It Works, Why Important, and When to Use It
18 June 2025
7
min read
Want to Switch to a New eID Provider?


Want to Switch to a New eID Provider?
28 January 2025
2
min read