Verifiable Information: An EU initiative to increase trust and reduce cost
By Niels Flensted-Jensen on 20 November 2025
8 min read
In the era of hyperscaling AI, the balance between capital and labor is tilting more than ever before. And capital — as any Marxist or modern economist will tell you — is concentrated in fewer and fewer hands.
The capitalists of our time are launching rockets, chasing techno-utopias, and asking for trillion-dollar pay packages. At the same time, here on Earth, common diseases may spiral out of control, and the climate continues to deteriorate.
Finally, tech billionaires oversee major social media platforms and powerful AI systems, which grant them significant influence over how information is distributed and accessed.
This is the backdrop against which young people must navigate the digital realm. This is our collective challenge. And this is not by any standard or measure a one-person or one-company challenge. It can't be, and it shouldn't be.
This challenge requires all of us to contribute to the best of our abilities. As the saying supposedly goes at AP Møller-Mærsk, "Den der har evnen har pligten." In English: "The one who has the ability, has the duty to apply it.”
A very particular set of skills

And like Liam Neeson, some of us have a very particular set of skills. We know how digital identity can unlock trust in a world of noise.
We can’t singlehandedly regulate AI. We can’t force platform accountability. But we know how to build infrastructure for trust— largely independently of the underlying tech stack.
Infrastructure that allows people — and systems — to know who they’re dealing with, what can be trusted, and where information comes from.
The era of information we can trust
That foundational layer is digital identity and what we like to call Verifiable Information.
The one new, easily identified component is the digital wallet, which holds these new pieces of verifiable information. Technically, the items in the wallet are referred to as Verifiable Credentials.
It is neither a surveillance tool nor a bureaucratic nightmare. It is an empowering new infrastructure for people, businesses, and institutions. And for once, Europe has not just a say — we have a head start.
In the Nordics, we know what trust in our societies feels and looks like. We know the benefits of allowing ourselves to trust our governments and private organizations. This level of trust—and more—is now also available online as the new wallet-centered infrastructure rails are being rolled out. To reap the benefits, we must, of course, stay out of the legal and technical weeds and strike the right balance between convenience and security.
So let's take a closer look. Where is the beef?
The beef is in the new generic information sharing rails being put in place by a wide range of governments and private companies.
The new wallet-centered infrastructure holds incredible potential, not just for high-confidence identification but also for broader trust-based information sharing.
But first, to make things more practical, let's consider the current eID information flow.
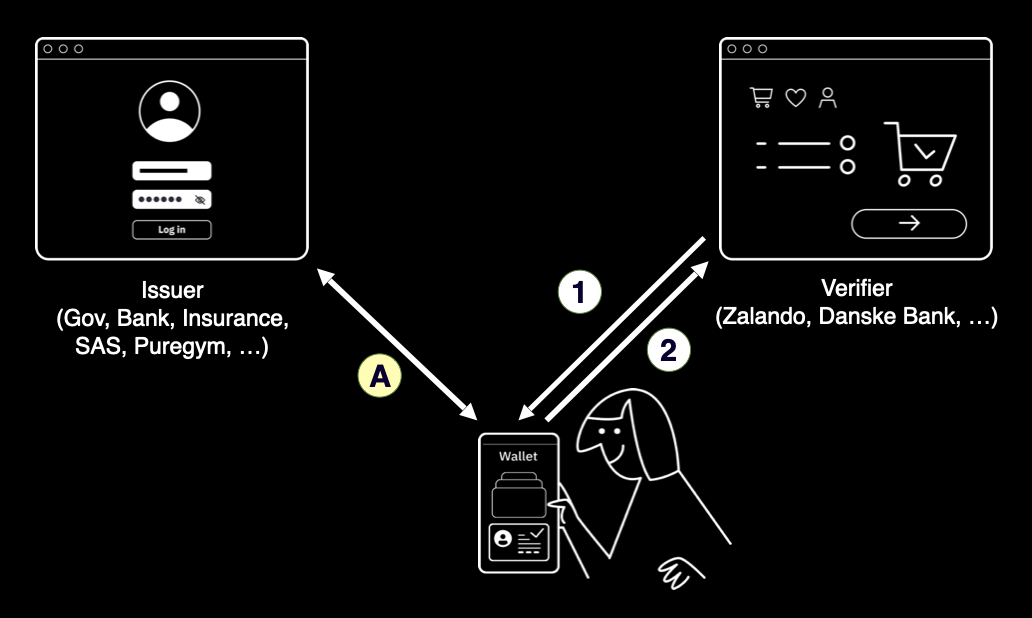
The federated identity model data flow
The diagram below illustrates the so-called federated data flow that runs behind the scenes whenever you use your digital identity, such as MitID or BankID.

You visit a service provider (like a bank or online shop) and are redirected to your eID provider to authenticate. After confirming your identity, you’re sent back to the service provider, which receives proof of authentication.
For a real-world analogy of this data flow, imagine you’re out barhopping in Copenhagen. You walk up to the first bar, and the bouncer asks to see your ID. You hand over your passport or driver’s license, he checks your details, then calls the police to report that he’s letting in someone with your name and social security number. The police dutifully write it down in their log, keeping a record of everyone enjoying the nightlife that evening.
We would, of course, never accept such surveillance in the real world. But that's precisely how it works online.
Thankfully, this is changing due to the new wallet-centered data flow and its asynchronous exchange of verifiable information between the issuers and the verifiers. The digital wallet is what enables this asynchronicity.
The wallet-centered data flow
In a wallet-centered data flow, an issuer—whether it’s a government agency, an insurance provider, or even your local gym—issues a credential to your digital wallet. You can present that credential to any verifier that accepts it. The issuer and verifier never communicate with each other; you’re the one in control, deciding exactly what information to share and with whom.

That's how it will work once we all use our digital wallets, at least in theory. We will no longer have any central monitoring of who we share our identity and other digital proofs with, leading to greater actual privacy.
The wallet-centered infrastructure is more robust, as no central service is involved in every transaction, unlike the current eID approach.
What we get with this new "issue–hold–present" paradigm is a new set of generic rails for sharing information that machines can verify. And that's important. Due to the cryptographic nature of the data structures and flows, the entire verification burden shifts to the machines.
Each credential is digitally signed by the issuer, which allows your wallet—and any verifier—to check its authenticity without contacting the issuer directly. Trust doesn’t come from a central authority constantly validating transactions; it comes from the mathematics of cryptography. Verifiers can independently confirm that the credential hasn’t been tampered with, that it was issued by a trusted source, and that it’s still valid. In other words, trust shifts from relying on intermediaries to relying on cryptographic guarantees.
That's what the updated eIDAS 2 is all about. eIDAS 2 narrows down the requirements for participating in these data flows in government-related contexts, while also working closely with, for example, the payments sector to ensure broad private backing and applicability.
If the authorities regulate your specific use case, you may need to comply explicitly with the eIDAS requirements. But if formal requirements do not bind you, maybe because your business is more mundane, you will still benefit from the new paradigm. In this case, you won't have to prove yourself to a certification body, and you won't be restricted to issuers, wallets, and verifiers formally approved in the EU eIDAS context.
Verifiable Information
We’ve seen how in this new era of verifiable information, cryptographic trust becomes a part of the infrastructure. Data origin, data integrity, the subject of the data, and the holder of the data—proof of all this is embedded in the infrastructure and the cryptographic nature of how the information is packaged.
This is a new way of handling information.
In the past, we trusted the information simply because we trusted the channel over which it arrived. The channels were bespoke and differed from issuer to issuer: each source had its own way to access and retrieve data.
As an example, consider the Danish registry of motor vehicles, DMR. Danish insurance companies have a direct API integration that lets them extract vehicle data on your behalf. This type of information exchange is easily facilitated by issuing a so-called credential to the vehicle owner, who keeps it in her digital wallet. The vehicle credential can then—at will and with full consent—be shared with any interested party, such as the insurance company.
Notably, this exchange will happen over the wallet infrastructure rails. This approach has all the cryptographic qualities we discussed: It proves the issuer is who they claim to be, the information is intact, and the vehicle owner is indeed the one presenting the credential. And not least, the information sharing happens with the owner's full consent.
So, after this section on data flows and wallets, we ask again: Where is the beef?
The benefits of trust infrastructure
As we saw earlier, the new data model forms a trust infrastructure for companies and organizations to build upon.
If your company is a credible or authoritative source of information, you may issue that data as Verifiable Information for others to use. Maybe you want to issue an insurance policy, a loyalty program, or a membership card.
Lower cost for verifiers
When a user later presents this information to a website, verification is automatic and happens without human participation. This directly lowers the cost for the Verifier who sees the insurance policy, proof of address, proof of bank account details, or other data. For the Verifier, the benefit is right there, and the cost savings can be shared with the customer.
For the issuer, the benefit varies with the use case. Let’s take, for example, a gym membership where the gym both issues and verifies the credential. The benefit is in not having to invent new verification methods; the membership "card" is tied cryptographically to the actual member, etc.
Sometimes, the user might be the one paying for a credential in their wallet, such as an airport VIP lounge access card.
Risk reduction for everyone
But another, concrete benefit of increased trust is the inherent risk reduction.
Companies adopting this emerging infrastructure may greatly benefit from the lower risk involved in the issuance, presentation, and verification of Verifiable Information.
The fact that machines can perform a complete verification through clever combinations of readily available cryptography and protocols has a substantial impact. A machine may verify that a piece of information originates from a trusted source (the Issuer), concerns a specific person, and is, in fact, presented by that person.
No longer do bank employees need to verify that I do indeed live where I claim to live or have the phone number I claim to have. No longer does the auto rental company need you to email or upload a picture of your driver's license, which may or may not be genuine. These and many more scenarios are now subject to automatic, high-confidence verification.
As a whole, this lowers the risk temperature in society while helping companies benefit from reduced costs and prices. But this will eventually spread far beyond these transactional use cases.
For example, camera makers and Adobe are working on issuing photos as verifiable credentials. This way, your browser may cryptographically verify that an image on the Internet originates from a specific Nikon camera and was touched up in Adobe Photoshop by the BBC.
In conclusion, while we wait for the entire Eurostack to materialize, a foundational layer of trust is already being built on top of whatever stack you apply.
In the early days of the Internet, the saying went, “On the Internet, nobody knows you’re a dog.” In the future, though, nobody on the Internet will think you are a dog. And, hopefully, no one will confuse a misleading piece of Russian propaganda with a valid contribution to democratic debate.
So, with that, please start thinking about how you can raise trust and lower the risk temperature in your corner of our shared world.
These Related articles

Why Caller Authentication is a Better Way to Verify Identity on the Phone

Digital Identity in Europe Depends on More Than Wallets
Practical Guide to FTN Compliance & the Idura Compliance Checker
Sign up for our newsletter
Stay up to date on industry news and insights