What Are Universal Links and App Links, and How to Implement Them


What Are Universal Links and App Links, and How to Implement Them
23 January 2026
8
min read
Idura Provides Qualified Electronic Signatures through Norwegian BankID


Idura Provides Qualified Electronic Signatures through Norwegian BankID
12 December 2025
1
min read
Verifiable Information: An EU initiative to increase trust and reduce cost
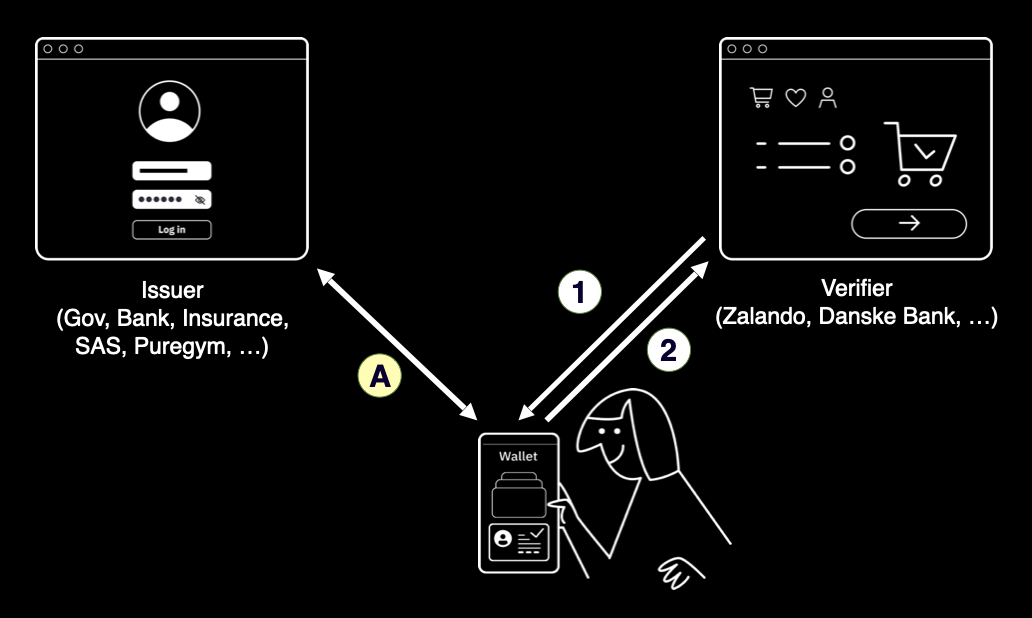

Verifiable Information: An EU initiative to increase trust and reduce cost
20 November 2025
8
min read
Connect 2025: Highlights & Takeaways from a Nordic Perspective


Connect 2025: Highlights & Takeaways from a Nordic Perspective
14 November 2025
10
min read
Criipto is now Idura

Criipto is now Idura
13 November 2025
2
min read
Why Caller Authentication is a Better Way to Verify Identity on the Phone


Why Caller Authentication is a Better Way to Verify Identity on the Phone
20 October 2025
2
min read
Digital Identity in Europe Depends on More Than Wallets


Digital Identity in Europe Depends on More Than Wallets
7 October 2025
2
min read
Idura: Certified FTN broker


Idura: Certified FTN broker
10 September 2025
2
min read
Practical Guide to FTN Compliance & the Idura Compliance Checker

Practical Guide to FTN Compliance & the Idura Compliance Checker
21 August 2025
3
min read
5 Reasons Verifiable Credentials Are Not Yet Widely Adopted


5 Reasons Verifiable Credentials Are Not Yet Widely Adopted
9 July 2025
3
min read
10 Use Cases for Verifiable Credentials


10 Use Cases for Verifiable Credentials
9 July 2025
4
min read
6 Business Benefits of Verifiable Credentials


6 Business Benefits of Verifiable Credentials
9 July 2025
5
min read