Multi-Factor Authentication: Definition, Use Cases, and Benefits


Multi-Factor Authentication: Definition, Use Cases, and Benefits
16 December 2024
5
min read
Passkeys: an Overview


Passkeys: an Overview
13 December 2024
7
min read
eIDAS Levels of Assurance in Different National eID Schemes


eIDAS Levels of Assurance in Different National eID Schemes
6 December 2024
4
min read
What is Authentication?


What is Authentication?
5 December 2024
6
min read
What is biometric authentication?

What is biometric authentication?
2 December 2024
5
min read
Zero-Knowledge Proofs: A Beginner's Guide
Zero-Knowledge Proofs: A Beginner's Guide
12 September 2024
10
min read
Getting Started with iDIN: The Complete Guide for Businesses


Getting Started with iDIN: The Complete Guide for Businesses
1 August 2024
3
min read
How to Authenticate Callers with Twilio, CIBA, and the Swedish BankID Phone Authentication


How to Authenticate Callers with Twilio, CIBA, and the Swedish BankID Phone Authentication
4 July 2024
10
min read
An Introduction to Client Initiated Backchannel Authentication (CIBA)

An Introduction to Client Initiated Backchannel Authentication (CIBA)
31 May 2024
4
min read
What Are SD-JWT-based Verifiable Credentials?


What Are SD-JWT-based Verifiable Credentials?
21 March 2024
7
min read
Verifiable Credentials: A Glossary (For Everyone)
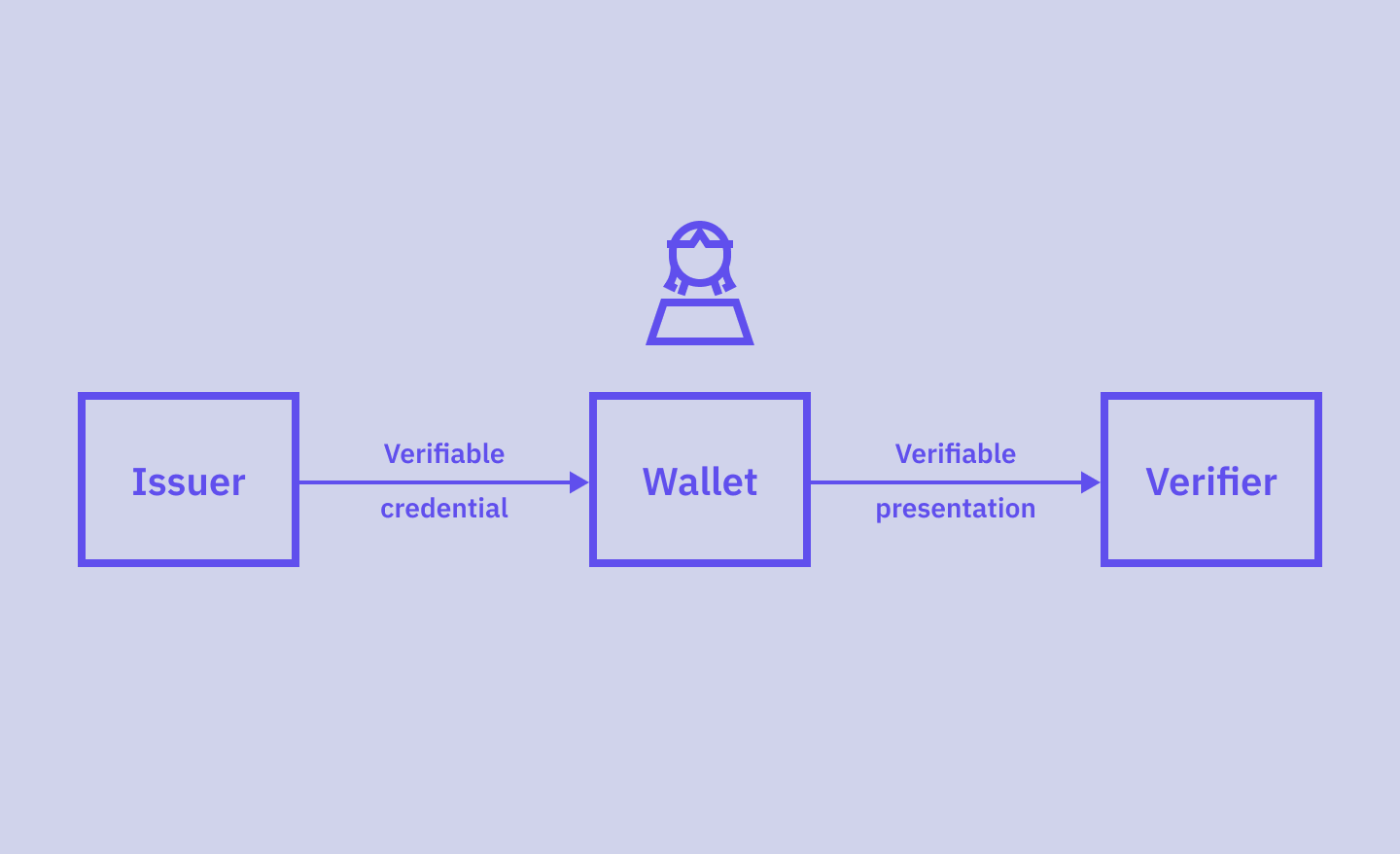

Verifiable Credentials: A Glossary (For Everyone)
1 March 2024
7
min read
Understanding JWT Validation: A Practical Guide with Code Examples


Understanding JWT Validation: A Practical Guide with Code Examples
22 January 2024
11
min read